Unmasking Black Basta: A Closer Look at the Notorious Ransomware Group
securityboulevard.com – 2023-06-20 05:29:19 – Source link

Who is Black Basta?
Black Basta (AKA BlackBasta) is a ransomware operator and Ransomware-as-a-Service (RaaS) criminal enterprise that first emerged in early 2022 and immediately became one of the most active RaaS threat actors in the world, racking up 19 prominent enterprise victims and more than 100 confirmed victims in its first few months of operation.
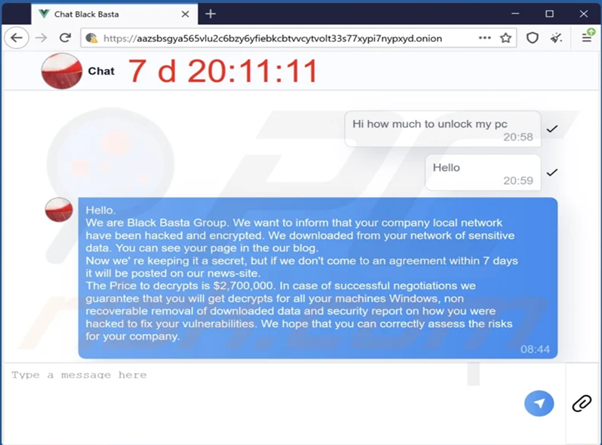
The group’s ransom tactics use a double extortion tactic, encrypting their victim’s critical data and vital servers and threatening to publish sensitive data on the group’s public leak site.

It is assumed that BlackBasta’s core membership to have spawned from the defunct Conti threat actor group due to similarities in their approach to malware development, leak sites, and communications for negotiation, payment, and data recovery.
ABB Ransomware
On May 7th, 2023, the Swiss multinational corporation ABB, fell victim to a ransomware attack conducted by the Black Basta ransomware gang, a cybercrime group that surfaced in April 2022.
The ransomware attack has affected the company’s Windows Active Directory, affecting hundreds of devices.
The security incident directly affected certain locations and systems.
In response to the attack, ABB terminated VPN connections with its customers to prevent the spread of the ransomware to other networks.
BlackBasta Ransomware Malware
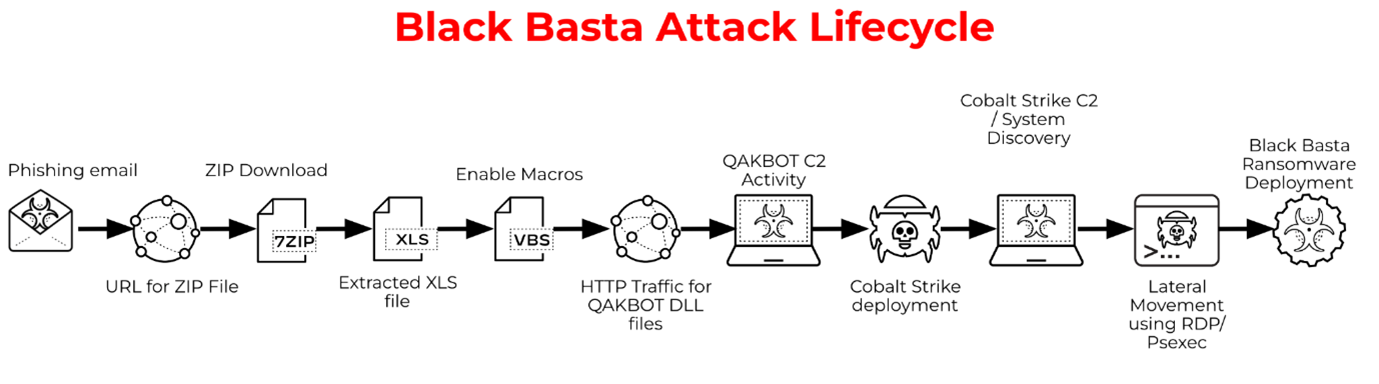
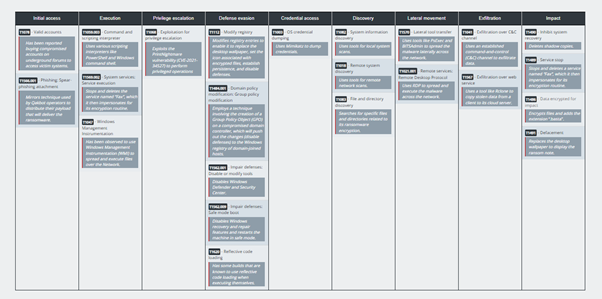
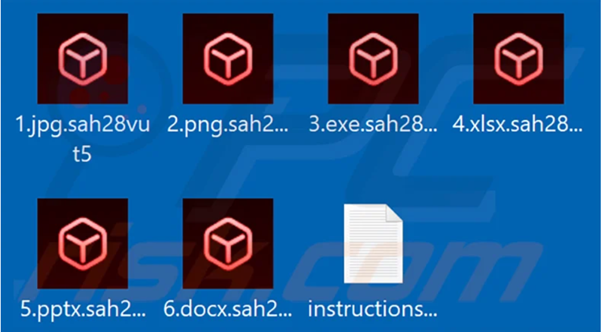
The ransomware is written in C++ and impacts both Windows and Linux operating systems. It encrypts users’ data using a combination of ChaCha20 and RSA-4096, and to speed up the encryption process, the ransomware encrypts in chunks of 64 bytes, with 128 bytes of data remaining unencrypted between the encrypted regions. The ransomware also attempts to delete shadow copies and other backups of files using vssadmin.exe, a command-line tool that manages Volume Shadow Copy Service (VSS), which captures and copies stable images for backups on running systems.

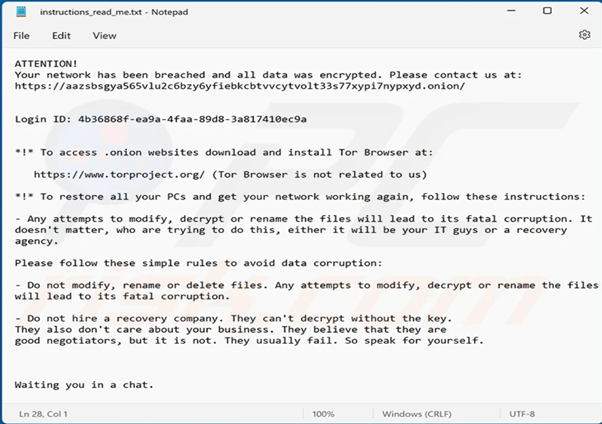
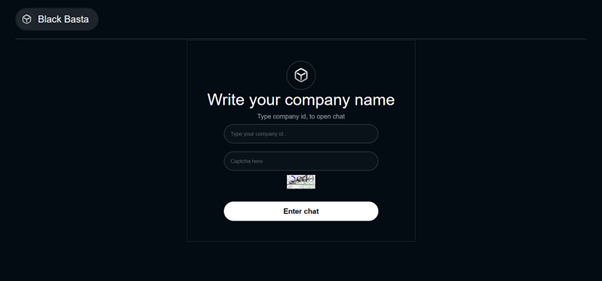
Link to the Black Basta Negotiation Site: hxxps://aazsbsgya565vlu2c6bzy6yfiebkcbtvvcytvolt33s77xypi7nypxyd.onion
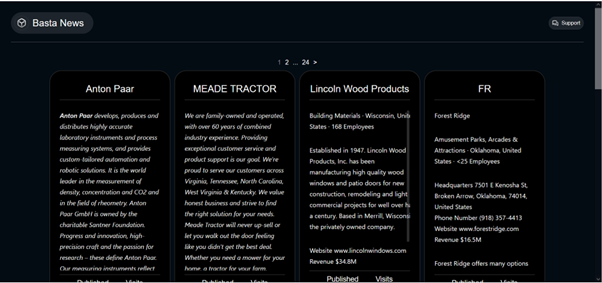
Link to the Leaks Site
hxxp://stniiomyjliimcgkvdszvgen3eaaoz55hreqqx6o77yvmpwt7gklffqd.onion
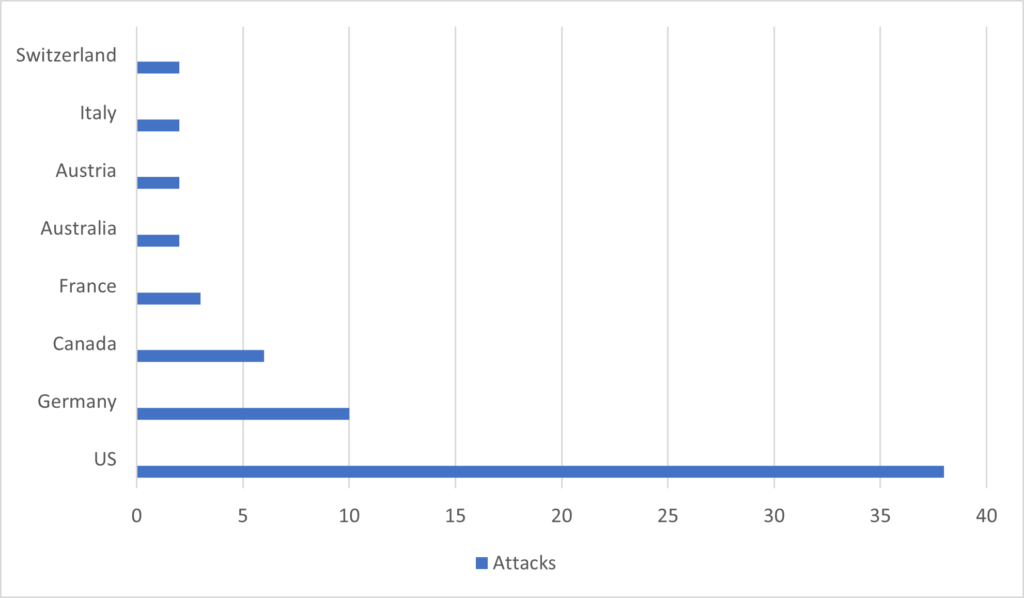
Black Basta Targeting Countries
The distribution by country of BlackBasta’s victim organizations from April 1 to July 31, 2022
This article is attributed to Vikas Karunakarn, Aditya Kirit Katpara, Akshay Jambagi & Dipanjali Rani from Sectrio’s threat research team.
Check out: The Global OT and IoT Threat Landscape Assessment and Analysis Report 2023

Reference:
- https://dxc.com/us/en/insights/perspectives/report/dxc-security-threat-intelligence-report/june-2022/black-basta-ransomware-emerges
- https://socradar.io/dark-web-profile-black-basta-ransomware/
- https://www.bleepingcomputer.com/news/security/multinational-tech-firm-abb-hit-by-black-basta-ransomware-attack/
- https://unit42.paloaltonetworks.com/threat-assessment-black-basta-ransomware/
- https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-blackbasta
- https://www.trendmicro.com/content/dam/trendmicro/global/en/research/22/j/black-basta-ransomware-gang-infiltrates-networks-via-qakbot,-brute-ratel-and-cobalt-strike/ioc-black-basta-infiltrates-networks-via-qakbot-brute-ratel-and-cobalt-strike.txt
*** This is a Security Bloggers Network syndicated blog from Sectrio authored by Sectrio. Read the original post at: https://sectrio.com/unmasking-black-basta-ransomware-group/





