Top 10 Best Practices for Zero Trust IoT Manufacturing
securityboulevard.com – 2021-01-21 21:47:14 – Source link
Internet of things (IoT) and industrial control system (ICS) devices are especially vulnerable to cyber-attacks due to weak security controls and vulnerabilities in the manufacturing supply chain. For example, automotive electronic control units (ECUs), the devices that control in-vehicle safety, drive train, and infotainment systems, are often manufactured in a sprawling supply chain that cannot be completely trusted. These automobile manufacturers are left with the challenging task of managing ECU security once the devices are installed and on the road.
Other critical infrastructure devices such as smart building control systems, fire and safety systems, traffic control systems, smart lighting, telematics devices, industrial controllers, medical devices, and smart meters are also vulnerable to compromise during the manufacturing process.
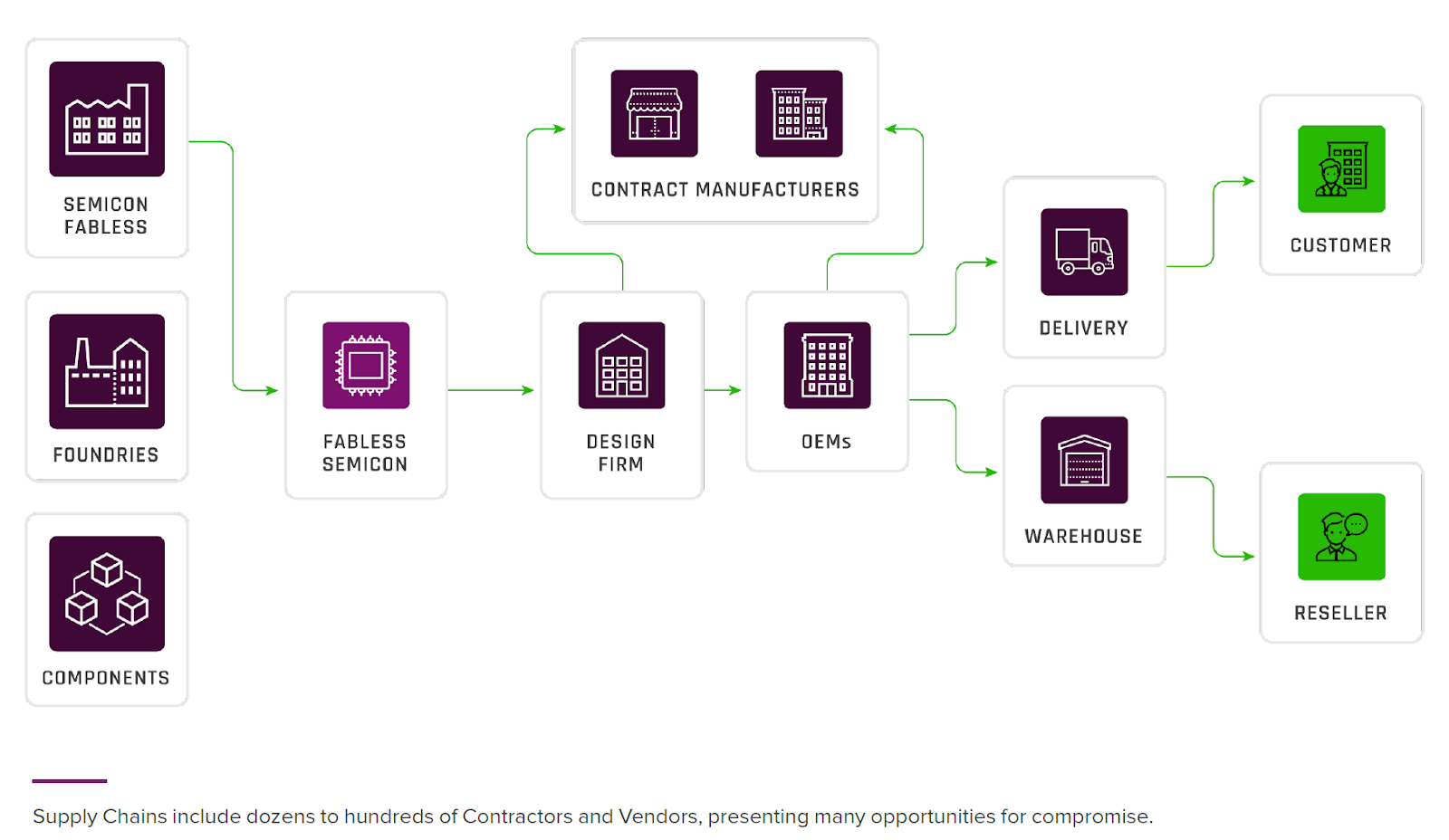
With literally thousands of original equipment manufacturers (OEMs), contract manufacturers, and software developers working together, ensuring that the devices themselves can be trusted can be extraordinarily difficult.
Product security weaknesses make it difficult for OEMs device operators and end-users to protect the safety, reliability, data privacy, communications, and the integrity of firmware over-the-air (FOTA) updates.
The solution? Taking a zero trust approach.
The 10 Best Practices for Zero Trust Manufacturing
Zero trust manufacturing is an approach to manufacturing trustworthy safety-critical devices along a supply chain that inherently cannot be trusted. Going beyond zero trust networking, this approach addresses supply chain weaknesses during the design, manufacturing, testing, and delivery of products.

If you are manufacturing or using IoT or ICS products and you need to start focusing on securing your supply chain.
#1 Root of Trust (RoT)
An RoT is a foundation upon which all secure computing operations are based. Installed on a device, an RoT contains the keys used for cryptographic functions and enables a secure boot process. Roots of trust can be implemented in hardware, which can offer very strong protection against malware attacks. An RoT can also be implemented as a security module within processors or a system on a chip (SoC).
#2 Hardware-based Secure Element
When possible, use a hardware-based secure element to create a root of trust (RoT). Leverage a tamper-resistant secure element such as a TPM or a network or cloud-based hardware secure modules (HSMs). TPMs provide secure key generation and storage that provide hardware-based, security-related functions.
#3 Generate on-device keys
Private and public keys used to identify the device should be generated and stored securely on the device so that the device can attest to its own identity. These keys can be used to for public-key cryptography, encryption, and code signing.
#4 Cryptographic software libraries
Integrate strong cryptographic libraries without known CVE vulnerabilities to handle crypto-operations such as encryption, TPM operations, and authentication.
#5 Enable mutual M2M authentication
The best way to establish trust between IoT endpoints is by utilizing mutual machine-to-machine (M2M) authentication, where both the client and server are authenticated. Implementing client-side certificate authentication, whereby the IoT device itself owns the private key, and only the public key is shared with the other party, is critical to ensuring the integrity and trustworthiness of the device. Avoid using pre-shared keys (PSK), which are highly vulnerable to theft.
#6 Automate the PKI Management Lifecycle
Managing the key and certificate lifecycle, including PKI, is the most complicated part of implementing managing device security. It is also the most important aspect of ensuring trusted devices. Ensure that you can automate:
- Secure key and certificate generation
- On-device certificate signing request (CSR) generation
- Key and certificate management changes
- Root signing ceremony
- Revocation
- Transfer of ownership
- End-of-life
#7 Centralize code signing and secure boot
Code signing is the process of digitally signing software executables and scripts to confirm the author and integrity of the software. It is important to ensure that firmware updates are signed by the developer and authenticated by the device before being installed. Replace the initial bootstrap certificate with an updated certificate to ensure the device boots up with the intended firmware.
#8 Root Certificate Authority (CA)
Implement an on-premise CA or third-party CA with certificates signed by a trusted root CA to provide a high level of trustworthiness along the chain of trust of digital certificates.
#9 Integrate Device Management
PKI lifecycle management tools should be integrated with the device management system (DMS), so that it becomes a seamless process to generate key pairs and update the PKI.
#10 Secure communication with end-to-end encryption
Implement encrypted SSL/TLS or IP VPN communications to ensure data privacy that leverages a secure and automated PKI lifecycle management approach.
It is difficult to manually integrate these PKI capabilities across a global supply chain to ensure that digital identities can be issued, updated, and managed.
Keyfactor Control provides a turnkey solution for automating the management of the IoT security lifecycle in complex manufacturing supply chains.





