OSEE, an Unexpected Journey – Security Boulevard
securityboulevard.com – 2023-09-01 03:00:00 – Source link
On August 22, I received this mail, stating that I’ve had
successfully pass the OSEE exam:

That email was the culmination of years of studying,
hard work and pushing my limits beyond of what I
could ever imagine.
The road to getting that email started when I achieved
the OSCE certification on 2020, then buying a spot in
the Advanced Window Exploitation (AWE) training on
London and two years of failed attempts to travel due
to world-wide quarantine, COVID, UK visa
constraints and the passing of The Queen.
But I will start with a summary of what is the
OSEE certification first and will dive in
details of the training and some insights and tips
of the exam.
OffSec Exploitation Expert (OSEE)
OSEE (OffSec Exploitation Expert) is an OffSec
certification, which is obtained after you complete
the course EXP-401: Advanced Windows Exploitation (AWE)
and pass a 72 hours grueling and hard exam.
I’ve known people who have the certificate back from
2009 and the course have received several updates since
it’s inception, with exploits for Adobe Flash Player
and the Windows Kernel for the most recent version of
that moment.
The latest update was announced on the private
OSEE certified channel on OffSec Discord’s server the
18th of September of 2021 by
Morten Schenk, one the
current instructors of AWE.
Quoting them during my training,
they said “we need to be constantly updating this course,
otherwise the contents wouldn’t be advanced enough”.
And that phrase summarizes what AWE is: the most advanced,
difficult and insane Windows exploitation training on
the market.
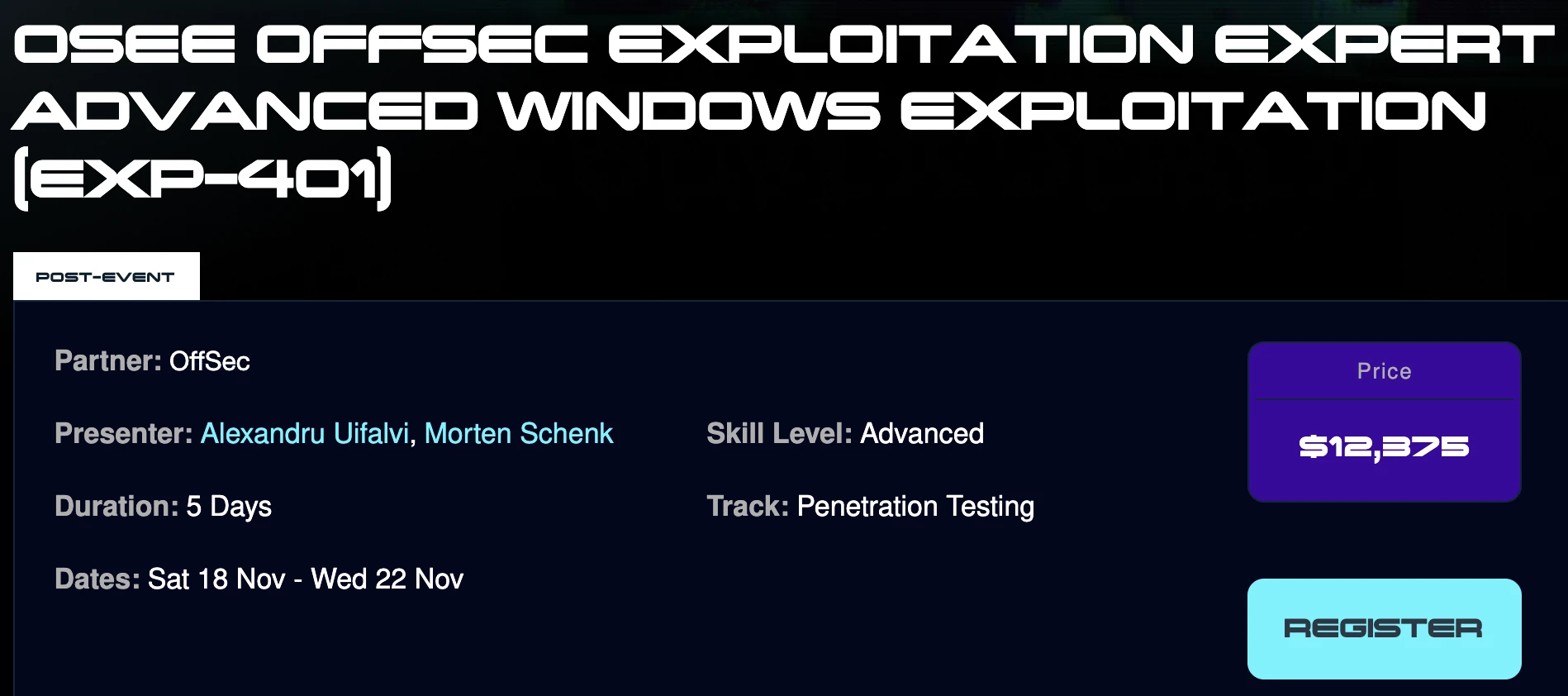
The current price for taking the course may vary according
the location. For example, on BlackHat Middle East and
Africa, the current price is $12,375:
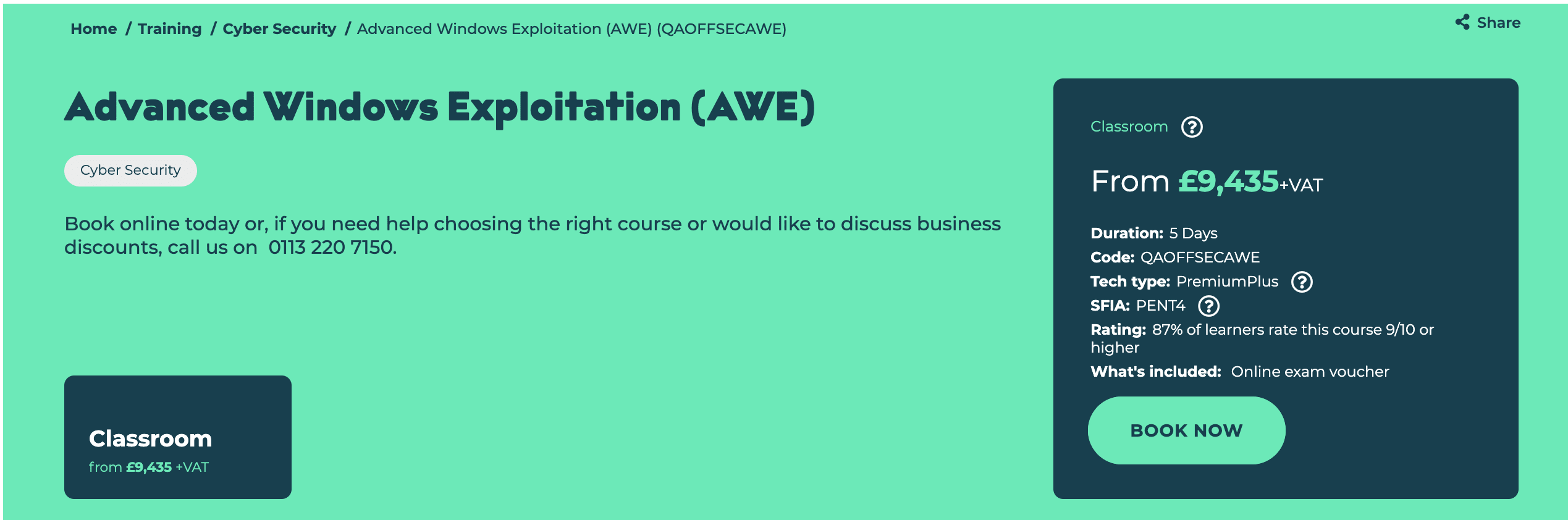
If you’re going to take it on London like me,
the current price is £9,435 + VAT:
A road to London
One of the main characteristics of the AWE
course is that you must attend in-person to the training.
Commonly, AWE is delivered on BlackHat USA in Las Vegas.
However, it was 2020 when I finished the
OSCE certification and BlackHat USA
was going to be 100% virtual due to the COVID pandemic.
I then look at the OffSec website and found that there
was a training on London going to happen on April of 2021.
I pulled the trigger but as expected, it was rescheduled
several times thanks to the pandemic. After several iterations
and a delayed UK visa, I was able to travel on September
2022 to take the course at the QA (a partner of OffSec)
installations in London.
The course was designed to be delivered in five days.
However, the monday that it was supposed to begin
was a bank holiday in the UK due to the funeral
of The Queen Elizabeth II. That resulted on an
intense four days brain melting training.
Course pre-requisites
As with all OffSec certifications, it is not required
to hold a specific title before attempting to take
any if their courses. However, as AWE is an advanced
training, they suggest to have:
- Experience performing dynamic analysis of binaries with
WinDbg and static analysis with IDA free. - Hands on experience of basic exploitation. You should
at least have written exploits in the past. - Basic knowledge on Windows x86_64 architecture and
x64 shellcode creation. - Familiarity with C/C++ programming and the use of
Visual Studio.
They also suggest to bring a laptop with a modern CPU,
at least 16GB of RAM and 160GB of free hard drive space.
However, when I arrived to the classroom, each student
had their own dedicated desktop PC with everything set up.
I’m not really sure if that is what happens on every
training but keep that in mind.
There is also a pre-training challenge upon
registration called 0h n03z, I @m bR0k3n!.
For this challenge, you are given a Visual Studio
project with a broken shellcode and you need to perform
dynamic analysis using WinDbg to fix it and make it pop a
calculator. They conclude with “solving this challenge
represents the minimal technical prerequisites required
for this course. If you find this challenge too
difficult, you may want to reconsider your registration
for the class”.
EXP-401
The official EXP-401 syllabus can be seen here.
One of the first slides of the training was this:
What could you expect of training that starts
like that? Well, you will be diving into five
modules where a detailed mindset for creating
complex exploits is outlined.
The first day, you create a custom x64 reverse
shellcode from the scratch. That sounds easy, right?
Well, that was given in the first 2 hours of the
training. The rest of the day was dedicated to
explain and complete a guest-to-host exploit
for a vulnerability in VMWare RPC mechanism
(called backdoor), bypassing modern exploit
mitigations like WDEG (which includes bottom-up heap
randomization) and an insane use of a mix of ROP + COP,
resulting with a reverse shell from the VMWare host.
The second day, a Type Confusion vulnerability on
Edge (pre-chromium) JS engine was presented.
Due to the nature of Edge and the security mitigations
presented, the road from the initial Arbitrary
Read/Write primitive to executing arbitrary Win32
APIs is plagued with controls including
CFG, ASLR, ACG, CET and DEP, which are bypassed using
mind-blowing techniques. To be able to
escape from the sandbox, a CVE is abused which
finally results on obtaining a reverse shell just
by clicking a button on a web page from the browser.
The third day was the start of Windows Kernel
exploitation. The first few hours were used
to explain how Kernel debugging was setup
and many important Windows internals concepts
relevant for exploitation, like Memory Paging,
SSDT, intro to Kernel Drivers, Kernel protections
among others. Then a LPE exploit is created for
a FortiShield driver vulnerability, creating
an Arbitrary Read/Write primitive, bypassing
SMEP by abusing the Page Table Entries (PTE),
restoring execution of the Kernel and
making it version-independent.
And finally the fourth day was spent on creating
an exploit for a native Windows driver (win32k).
The exploit performs heavy Pool manipulation and
a novel gadget for creating an Arbitrary Read/Write
primitive. Also, by abusing memory leaks, a version
of the exploit that works from a low integrity shell
is created. To push things further, the exploit is
updated to work even with HVCI enabled.
As a summary, the course will teach you to perform
a full chain exploit:
- Abuse a Type Confusion vulnerability to
obtain an Arbitrary Read/Write on a sandboxed Edge
process and execute arbitrary Win32 APIs. - Break out of the sandbox by exploiting
(reversing a C# exploit!) another Edge process and
running arbitrary OS commands in medium integrity. - Perform a guest-to-host attack by exploiting a
vulnerability on VMWare’s proprietary RPC
protocol. - Choose how to elevate privileges on the host OS,
by either exploiting a Fortinet driver or by
creating an exploit for the native win32k driver.
All of the above, bypassing advanced mitigations
like WDEG, CFG, CET, ACG, (k)ASLR, DEP, EAF, HVCI,
SMEP, …
Now, the WTF levels are easily understood.
Post-course hangover
As stated above, the course was four days long.
Unlike many other courses, the course material
includes two books with the written content
of the course, a ZIP file with all the PoC
created and the slides used to guide
the training. There are several extra miles
in the course (hint, hint!) that are there
to practice further on the topics presented.
Once the course is finished, you have up to
one year to schedule the exam. I scheduled mine on
August 17 of 2023.
The month before I was dedicated 100% to reprise
the course materials and reproduce the same
exploits:
Actually I read the materials twice during that month+
of study. The first time, I resolved all the
exercises of the five modules and did some
extra miles. The second time, I re-read all
the material but with a 30000 feet view to
get the big picture of the contents and
understand the design of the exploits
from a high level.
That approach gave me more confidence on
understanding and digesting the deep
level of technical concepts presented
on the course.
With everything set, the exam day arrived.
Exam
I booked the exam to start on August 17 of 2023 at 7am.
You have 71h and 45m of lab time to complete the
challenges and another 24h to create and upload a
report.
As the exam is proctored, you must show up 15 minutes
before for identity checking and other proctoring
checks.
The exam report template
provide guides on what to expect from the exam:
- Two challenges.
- On the first you must escape a sandbox.
- On the second you need to deal with the
Windows Kernel. - Each challenge can give 25 or 50 points.
- You must at least have 75 points to pass the exam.
- That means that you at least need to complete one
challenge and half of the other.
I can’t give more details on the exam, but I think
that the challenges are a good way to evaluate
the topics covered on the course and the time
is enough to complete them if you know what
you’re doing.
In my case, I finished the exam just about an hour
before the deadline. Yes, it was exhausting.
After a few hours of sleep, I created the report
and sent it the night of August 20. The last time
I submitted a report to OffSec was early this year
when I completed the OSEP
certification and I had to wait up to one week
for the results. However, just 2 days after submitting
the OSEE report, on August 22 I received the email
saying that I had passed the challenges and obtained
the OSEE certification.

Exam tips
The following are things that worked for me.
But as always, your mileage may vary.
- Complete all the exercises of the book.
- Each module have some extra miles. Complete
as much extra miles as possible.
The latest extra mile that I finished was the creation
of an exploit for CVE-2021-31956:
- Repeat points 1 and 2.
- I’ve done previous work
on Kernel Debugging. You can follow my blog
posts and replicate the
bypassing of controls and
creating an exploit for
HEVD. - The Browser Exploitation
series of Connor McGarr
are a good way to learn and
practice about the Edge Type Confusion module. - Join the OffSec Discord server.
The community is awesome,
and OffSec support personnel can assist you with anything
related with the course. - The VPN connection is not stable.
As it’s a UDP tunnel,
there can be problems with the MTU size calculation
(VPN MTU > Link MTU),
which can lead to packet loss during heavy traffic.
Follow this guide
to troubleshoot it.
In the end,
I had to add themssfix 1387line
to my OpenVPN connection file
to fix those issues.
Common criticism
First and most notoriously, attending the course is
expensive. However, in my most personal opinion, what
you learn during the training and preparation for
the exam is worth every penny.
Also, as the course name suggest, the training
is about exploitation. Microsoft have done a great
job since the releasing of Windows 8 to continuously
improve the security of the OS. And, even though the
course was updated on 2021, there are many techniques
presented on the training that not longer works in the
most current Windows OS versions. That means that although
the gained knowledge is more focused on creating the
mindset for making complex and advanced exploits,
some of the techniques and primitives used are not
longer valid and new research is needed for creating
an exploit for a modern Windows OS build (again,
in my opinion, this can even be an advantage if you
see it from other perspective).
Conclusions
The OSEE experience was really enriching for me.
Obtaining this certification was always a
personal dream and a ultimate goal for many other
fellow offensive security professionals.
But I’ve always had the same feeling after finishing
a certification: What’s next?
*** This is a Security Bloggers Network syndicated blog from Fluid Attacks RSS Feed authored by Andres Roldan. Read the original post at: https://fluidattacks.com/blog/osee-review/





