Centrify Automates Password Reconciliation via Client
securityboulevard.com – 2020-08-07 22:02:34 – Source link
Centrify has extended its password access management (PAM) service to enable password reconciliation on the client.
Torsten George, cybersecurity evangelist for Centrify, said enabling password reconciliation using Centrify client software in conjunction with version 20.3 of the Centrify Privileged Access Service eliminates the need for persistent administrative rights on a server, which reduces the overall number of privileged accounts that need to be created.
PAM services rely on rotation to ensure local passwords are in sync with the password vault. However, if someone changes a password, the vault and that machine will no longer be synchronized. The Centrify password vault can now perform a real-time check with the client to ensure the local password is as expected. If not, the password vault can change or reset the local password directly without requiring any intervention on the part of the IT staff or requiring a backdoor privileged account.
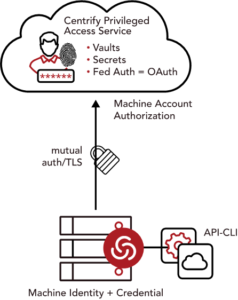 George said with employees and IT teams alike working from home, there is a greater need to automate password reconciliation issues, which IT teams historically have spent a significant amount of their time doing. At a time when many organizations have been forced to reduce the size of their IT staff, the Centrify PAM service automates a time-consuming task to give IT teams time to address more pressing issues, he said.
George said with employees and IT teams alike working from home, there is a greater need to automate password reconciliation issues, which IT teams historically have spent a significant amount of their time doing. At a time when many organizations have been forced to reduce the size of their IT staff, the Centrify PAM service automates a time-consuming task to give IT teams time to address more pressing issues, he said.
In general, the pandemic is requiring IT teams to rely more on the cloud to manage a slew of cybersecurity tasks. Like the other employees, cybersecurity teams are being asked to work from home as much as possible to help combat the COVID-19 pandemic. That becomes easier to achieve when relying on cloud services versus trying to access a console over a virtual private network (VPN).
It’s not clear whether organizations will prioritize PAM during the economic downturn brought on by the pandemic. However, it’s only a matter of time before auditors begin to ask questions about how passwords are being managed when most employees are working from home. A cloud service makes it easier to generate a report that can be shared with an auditor.
In the meantime, cybersecurity teams will be looking to automate as many processes as possible. Most organizations will not be expanding their IT staff. The number of cyberattacks focused on stealing credentials, however, continues to exponentially increase. Cybersecurity teams need to find a way to make sure whatever password change made wasn’t the work of cybercriminals who gained access to a system.
Rather than having to manually inspect all those password changes, the better part of valor is to automatically reset them. After all, when it comes to cybersecurity it’s always better to be safe than sorry, no matter who decided to change a password for whatever reason.





