
Microsoft
For years, Google and Mozilla have battled to keep abusive or outright malicious browser extensions from infiltrating their official repositories. Now, Microsoft is taking up the fight.
Over the past several days, people in website forums have complained of the Google searches being redirected to oksearch[.]com when they use Edge. Often, the searches use cdn77[.]org for connectivity.
After discovering the redirections weren’t an isolated incident, participants in this Reddit discussion winnowed the list of suspects down to five. All of them are knockoffs of legitimate add-ons. That means that while the extensions bear the names of legitimate developers, they are, in fact, imposters with no relation.
They include:
NordVPN
Adguard VPN
TunnelBear VPN
The Great Suspender
Floating Player — Picture-in-Picture Mode
“I had the tunnelbear extension installed, but I removed it once I figured out it was causing the issue,” Laurence Norah, a photographer at Finding the Universe, told me by email. “It’s easy enough to see it happening—if you install one of the affected extensions in Edge, open dev tools, and press the ‘sources’ tab, you’ll see something that shouldn’t be there like ok-search.org or cdn77.”
His account was consistent with images and accounts from other forum participants. Below are two screenshots:
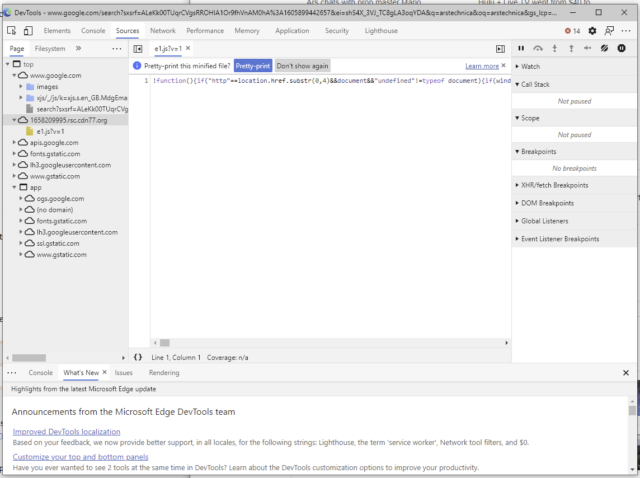
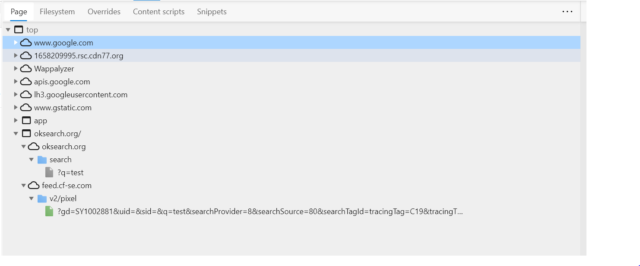
Microsoft officials have yet to provide a response to email seeking comment for this post. But in This Reddit comment someone identifying herself as a community manager for Microsoft Edge said the company is in the process of investigating the extensions.
“The team just updated me to let me know that anyone seeing these injections should turn off their extensions and let me know if you continue to see them at that point,” the person using the handle MSFTMissy wrote. “Once I have any news from them, I will update this thread accordingly.”
The maker of the legitimate TunnelBear software and browser extensions told me that the add-on hosted in Microsoft’s official Edge store is a fake. It said there’s an extension in the Chrome Web Store that’s also fraudulent.
“We are taking action to have these removed from both platforms and investigating the matter with both Google and Microsoft,” a TunnelBear representative said. “It is not uncommon for popular, trusted brands like TunnelBear to be spoofed by malicious actors.”
None of the remaining four legitimate developers of the real extensions responded to a request for comment. Readers should remember, however, that legitimate developers can’t be held responsible when their apps or add-ons are spoofed.
Along with Android apps, browser extensions are one of the weak links in the online security chain. The problem is that anyone can submit them, and Google, Mozilla, and now Microsoft haven’t come up with a system that adequately vets the authenticity of the people submitting them or the safety of the code.
Search engine redirections are typically part of a scheme to generate fraudulent revenue by ginning up ad clicks, and that’s what’s likely happening here. While reports indicate that the add-ons do nothing more than hijack legitimate searches, the privileges they require provide the possibility of doing much worse. Usage rights include things like:
- Reading and changing all your data on the websites you visit
- Managing your apps, extensions, and themes
- Changing your privacy-related settings
Anyone who has installed any of the above-mentioned Edge add-ons should remove them immediately. And the oft-repeated advice about browser extensions still applies here: (1) install extensions only when they provide true value or benefit and even then (2) take time to read reviews and check the developer for any signs an extension is fraudulent.
Post updated to add comments from TunnelBear.





