2023 cybersecurity forecasts: Zero trust, cloud security will top spending
venturebeat.com – 2022-12-20 18:07:00 – Source link
Check out all the on-demand sessions from the Intelligent Security Summit here.
Current predictions for cybersecurity spending in 2023 are reinforcing some of 2022’s top trends.
Gartner predicts zero trust network access (ZTNA) will be the fastest-growing network security market segment worldwide. It’s forecast to achieve a 27.5% compound annual growth rate (CAGR) between 2021 and 2026, jumping from $633 million to $2.1 billion worldwide.
U.S.-based growth of ZTNA software and services revenue reflects this strong market momentum, increasing from $318.9 million in 2021 to $1.04 billion in 2026.
Another projection from Markets and Markets has worldwide spending on zero trust-based software and services growing from $27.4 billion in 2022 to $60.7 billion by 2027, attaining a CAGR of 17.3%.
Event
Intelligent Security Summit On-Demand
Learn the critical role of AI & ML in cybersecurity and industry specific case studies. Watch on-demand sessions today.
Watch Here
Ninety-seven percent of companies either have a zero-trust initiative in place or will have one in the coming 12 to 18 months. That’s based on interviews with 700 security decision-makers who are director-level and above. It was up from 16% just four years ago and 41% in 2020.
Zero trust: Now a no-brainer
Zero trust gains momentum in the enterprise
Zero trust is gaining momentum across the enterprise, as CISOs face many challenges. These include securing identities as well as managing increasing complex cloud configurations and a proliferating endpoints base. Ninety percent of enterprises migrating to the cloud are adopting zero trust. And two-thirds (68%) of those senior cybersecurity leaders say secure cloud transformation is impossible with legacy network security infrastructure such as firewalls and VPNs.
>>Don’t miss our new special issue: Zero trust: The new security paradigm.<<
“Zero trust is being considered or deployed by most enterprises, so the debate on the need for zero trust is over; however, well over half will fail to see the benefits,” Kapil Raina, VP of zero trust, Identity, and data security marketing at CrowdStrike told VentureBeat. “To overcome these challenges, enterprises must operationalize and make zero trust frictionless, with a single platform and single sensor architecture — endpoints, workloads and other technology areas.”
“The days of castle-and-moat networking and perimeters are gone. Identity is the new perimeter,” said John McLeod, CISO of NOV Inc., in Okta’s State of Zero Trust Security 2022.
CISOs also tell VentureBeat that one of the most effective strategies for protecting and growing their budgets in the latter half of 2022 has been to show how zero trust protects revenue. Insights from interviews with CISOs identified where they are getting quick zero-trust wins today to save tomorrow’s budgets.
Getting zero trust right as part of a broader initiative to consolidate tech stacks and improve cost control and security effectiveness is a strategy CISOs are also using to improve their careers. Showing how their teams can drive revenue and protect it with zero trust is a career move that will lead to CISO promotions to board-level roles.
Gartner’s 2022 Market Guide for Zero Trust Network Access, provided courtesy of Absolute Software, is noteworthy in providing insights into what CISOs need to know about zero-trust security.
The following is a curated list of the most recent cybersecurity forecasts and market estimates:
Zero trust network access (ZTNA) will be the fastest-growing segment in network security, projected to grow 36% in 2022 and 31% in 2023.
Gartner predicts ZTNA demand will increase as enterprises look to provide zero-trust protection for remote workers, and organizations reduce dependence on VPNs for secure access. Gartner states that, “as organizations become familiar with ZTNA, there is a growing trend to use it not only for remote working use cases but also for workers in the office.”
Gartner predicts that by 2025, at least 70% of new remote access deployments will be served predominantly by ZTNA as opposed to VPN services, up from less than 10% at the end of 2021.
PAM and IAM
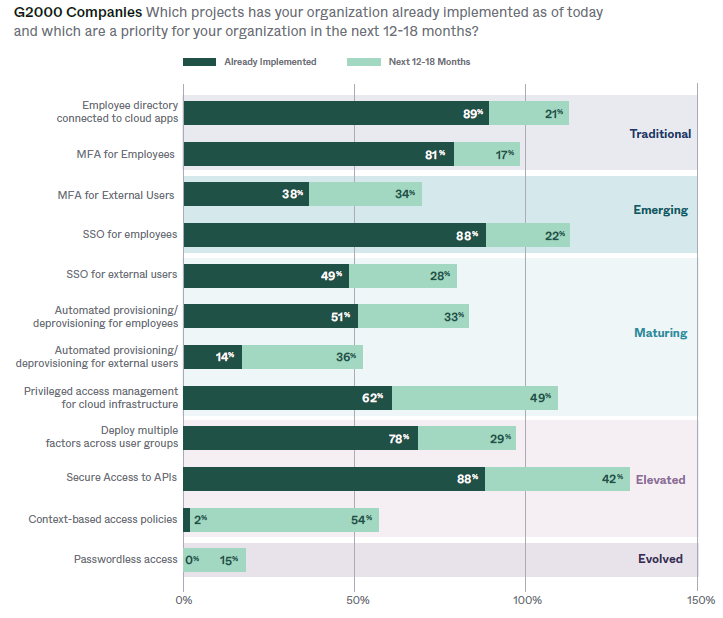
Privileged access management (PAM) for cloud infrastructure, secured access to APIs, and context-based access policies are the highest zero-trust priorities for Forbes Global 2000 (G2000) companies next year.
As large-scale enterprises began investing in a ZTNA strategy, they were quick to protect identities using proven technologies that deliver value. CISOs have told VentureBeat that getting the traditional and emerging classes of protection right is a proven way to protect their budgets because they can point to quantified results. Okta’s survey shows where enterprise CISOs who lead Global 2000 cybersecurity teams are concentrating their efforts and their spending in the next 12 to 18 months.
IBM researchers warn that cyberattackers are devising new, innovative techniques to exploit MFA and EDR technologies, making 2023 another challenging year for cybersecurity teams and CISOs who lead them.
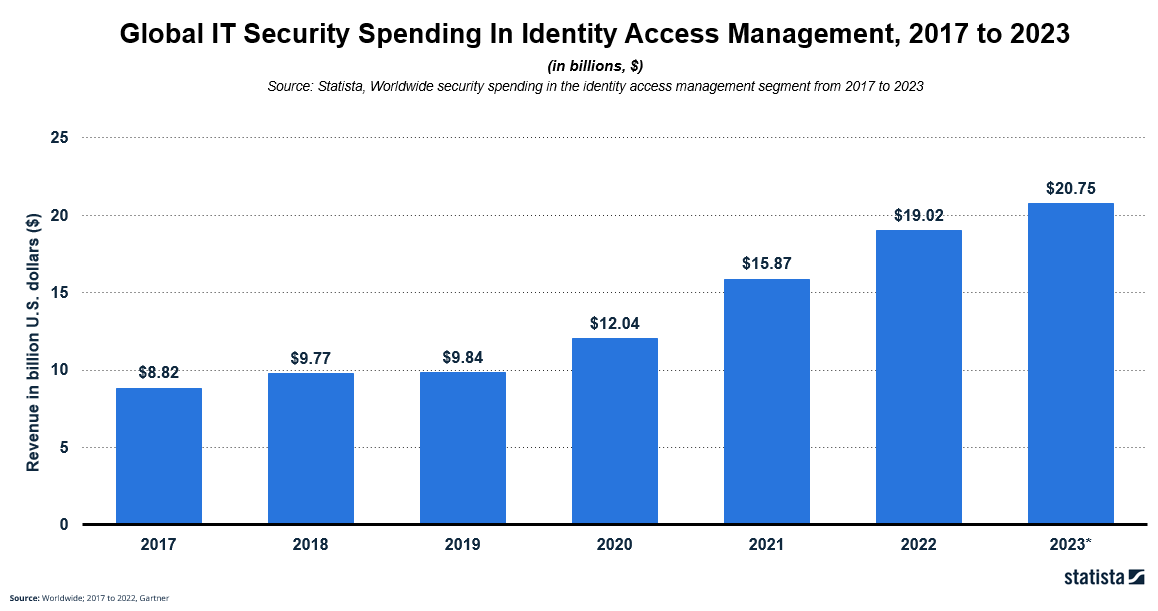
Meanwhile, worldwide spending on Identity Access Management (IAM) software and solutions will reach $20.75 billion next year.
Identities are the security perimeter most easily breached by attackers, who either steal privileged access credentials or target Privileged Access Management (PAM) systems to gain administrators’ identities and take control of a network. “Eighty percent of the attacks, or the compromises that we see, use … some form of identity, credential theft,” CrowdStrike CEO George Kurtz told the keynote audience earlier this year at the company’s Fal.Con conference.
Thwarting credential theft with a passwordless authentication system is working. Leaders in the field include Ivanti, OneLogin Workforce Identity and Thales SafeNet Trusted Access.
Of these solutions, Ivanti’s Zero Sign-On (ZSO) approach is noteworthy in how it combines passwordless authentication and zero trust on the Ivanti Unified Endpoint Management (UEM) platform. Ivanti ZSO, a core component of the Ivanti Access platform, replaces passwords with mobile devices as the user’s Identity and primary factor for authentication. ZSO eliminates the need for passwords using FIDO2 solid authentication protocols. CIOs tell VentureBeat that improving IAM integration in collaboration with CISOs is a high priority and core to their ZTNA initiatives to secure every identity, threat surface and endpoint corporate-wide.
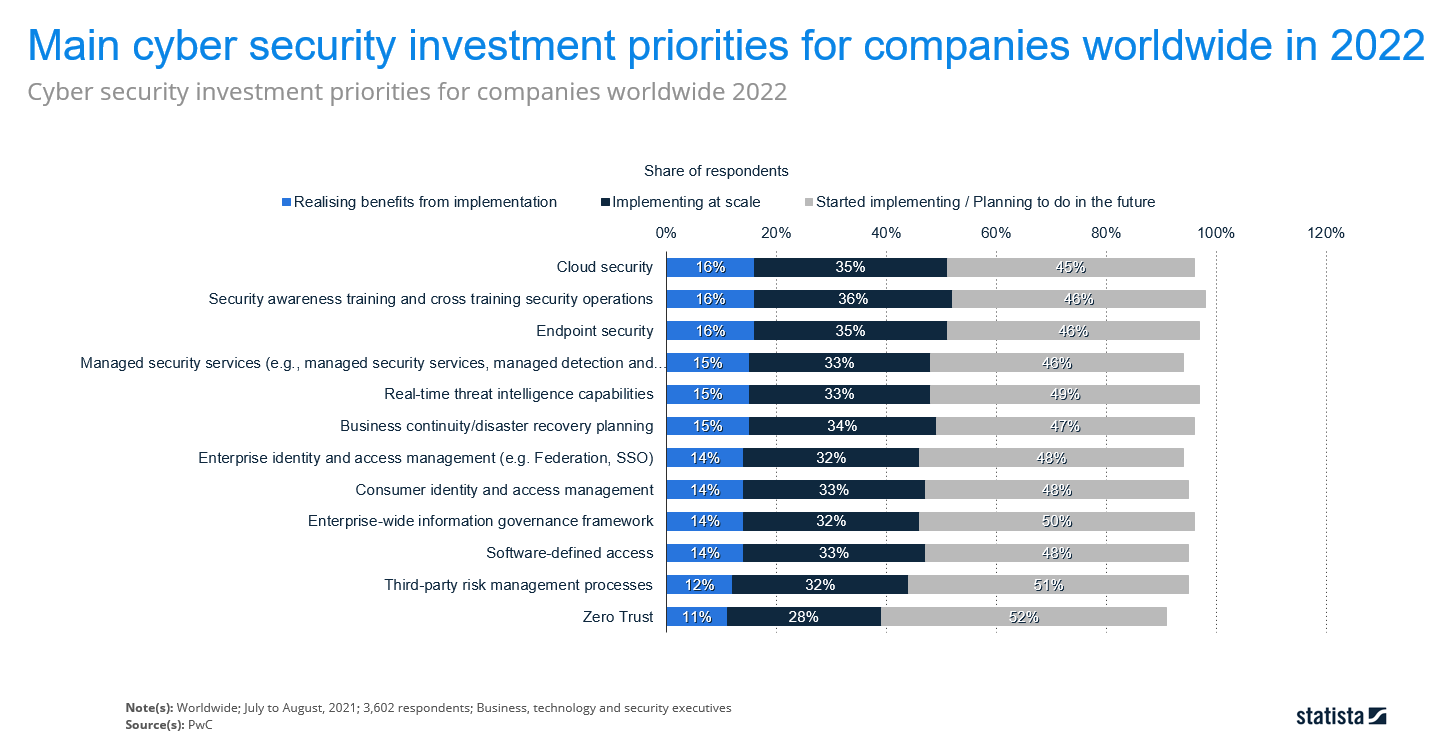
Cloud adoption on the rise
Sixteen percent of enterprises are already realizing benefits from investing in cloud security, security awareness training and endpoint security this year.
Half of the enterprises interviewed by PwC say they have started planning and implementing an enterprise-wide information governance network. That’s consistent with what CISOs have told VentureBeat throughout the year. They’re looking to use governance as guardrails in consolidating their tech stacks. 50% of those enterprise security leaders have either started implementing or are planning to implement zero trust. By 2023, 40% of all enterprise workloads will be deployed in cloud infrastructure and platform services (integrated and standalone), up from 20% in 2020.
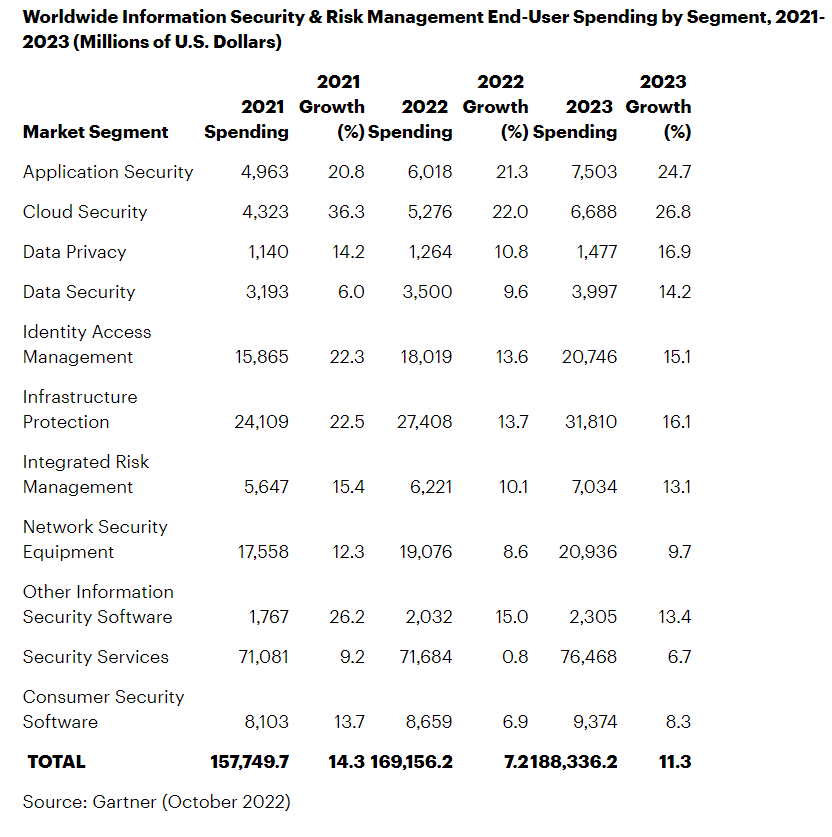
Spending on information security and risk management products and services is forecast to grow 11.3% to reach more than $188.3 billion in 2023.
Gartner predicts cloud security will see the fastest growth over the next two years, attaining a 26.8% growth rate in 2023. “The pandemic accelerated hybrid work and the shift to the cloud, challenging the CISO to secure an increasingly distributed enterprise,” said Ruggero Contu, senior director analyst at Gartner. Security services, including consulting, hardware support, implementation and outsourced services, are the largest spending category, at almost $72 billion in 2022, expected to reach $76.5 billion in 2023.
Budgets, vendors under strain
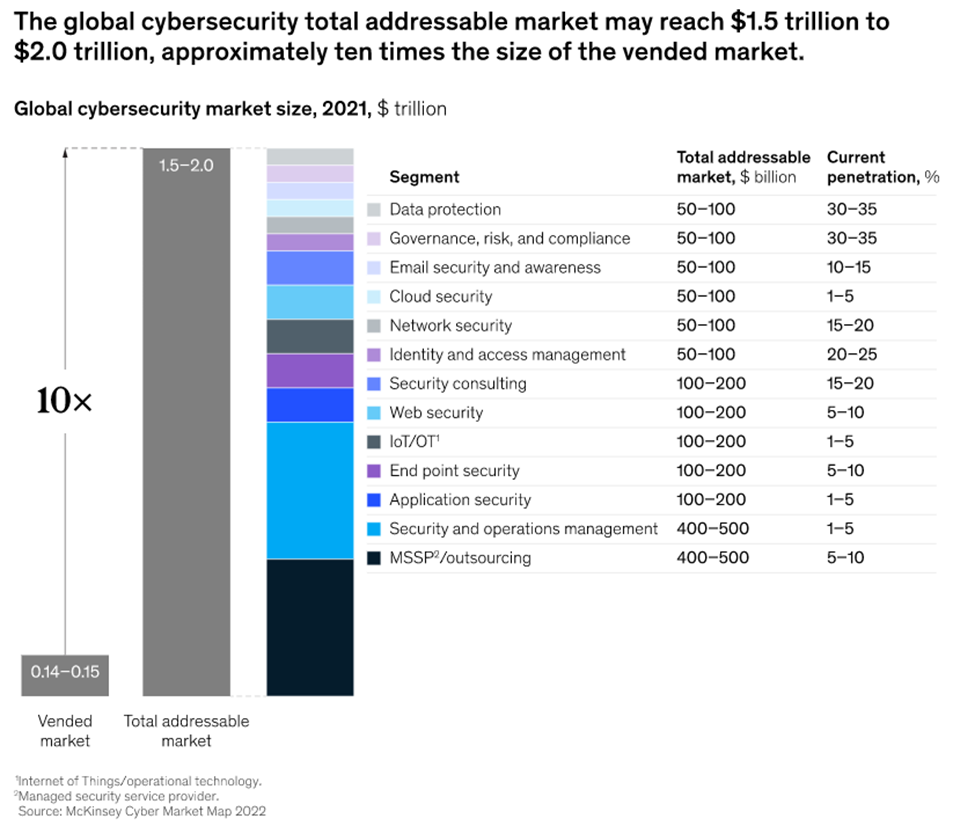
Global cybersecurity has a potential total addressable market (TAM) size of between $1.5 and $2 trillion, with just 10% served by security solutions vendors today.
McKinsey’s recent survey defines an exponentially larger TAM than vendors can address. This is due to the exponential growth and severity of cyberattacks. At best, 30 to 35% of the data protection and governance, risk and compliance market is served.
McKinsey estimates that up to 25% of organizations’ identity and access management (IAM) cybersecurity requirements can be met with the current base of vendors. McKinsey’s authors’ comment that the results “suggest that the budgets of many if not most chief information security officers (CISOs) are underfunded. Cybersecurity providers must meet the challenge by modernizing their capabilities and rethinking their go-to-market strategies.”
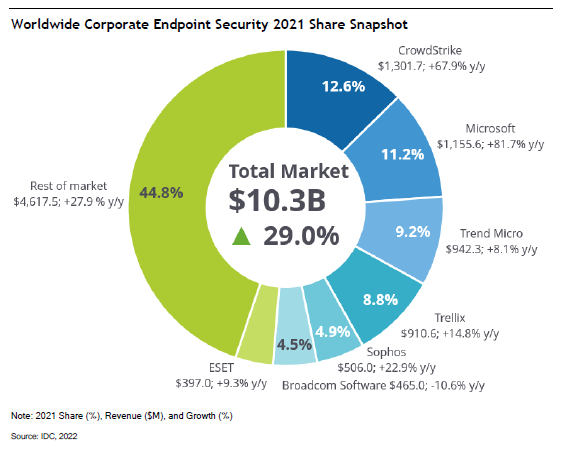
Endpoint security a large growth area
The worldwide corporate endpoint security market increased by 29.0% in 2021, with revenue increasing by $2.3 billion from $8.0 billion in 2020 to $10.3 billion in 2021, according to IDC.
According to the report, CrowdStrike owned “12.6% of the $10.3 billion corporate endpoint security market in 2021, demonstrating 67.9% year-over-year growth.” CrowdStrike continued to be the largest vendor in the modern endpoint security submarket, pushing its 12.0% market share in 2020 to 15.5% in 2021.
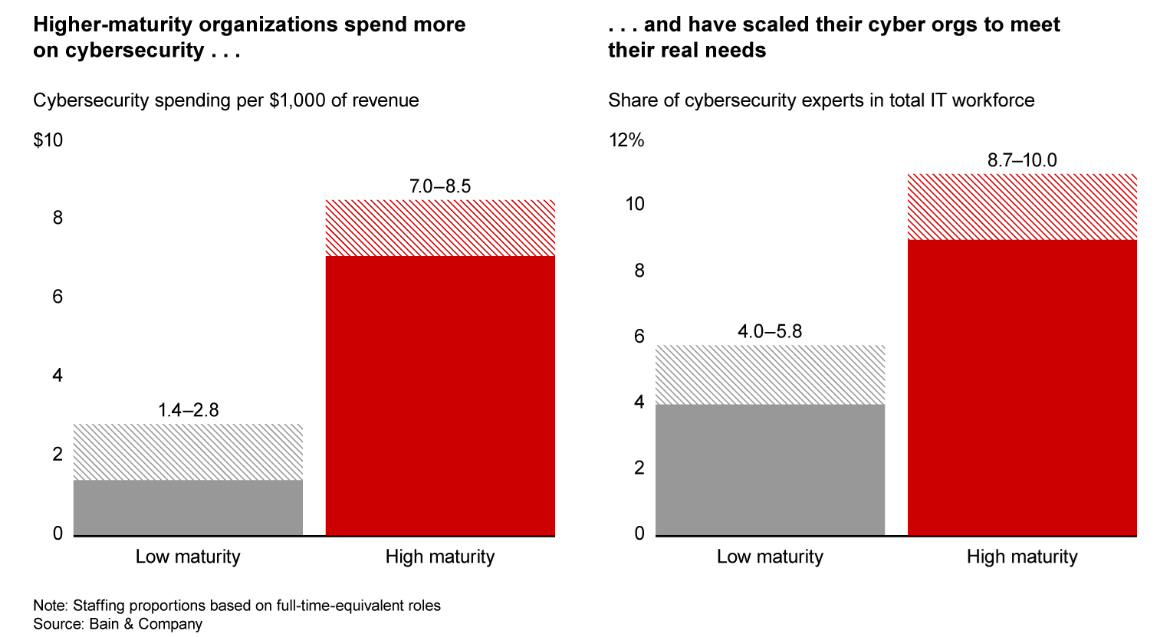
Three percent of CISOs believe they are meeting best-practice levels of cybersecurity, while 24% of companies actually meet the standard.
Bain and Company’s recent analysis of its cybersecurity best practices survey shows that CISOs and senior security leaders are underestimating the risks of not adequately focusing on attaining cybersecurity best practices. Bain’s analysis found that on a cybersecurity maturity scale of 1 to 5, a typical company is likely to rate only 1.5 to 2.5, significantly below what Bain’s analysis shows is a best-practices level of risk and security management.
The company notes in the report that one factor is that “industry frameworks such as NIST and ISO 27002 are an essential building block of cybersecurity. But to protect themselves fully amid such global instability, companies need to go beyond checklist-focused implementation of the best practices enshrined in these frameworks.”
A more focused and prioritized effort is needed to tailor zero trust to enterprises’ current and future business challenges.
2023’s cybersecurity challenges will test companies’ resilience
C-level executives and boards of directors say a catastrophic cyberattack Is the top scenario in their 2023 resilience plans. Preparing for a worst-case risk scenario at that scale needs to start with treating cybersecurity spending as a business decision.
PwC’s 2023 Global Digital Trust Insights Survey also found that more than half of CEOs now require a cyber-risk management plan for each business unit. They’re also eliminating products and supply chain operations that weaken their company’s security posture.
Underscoring all these findings is that C-level executives and boards now realize that underestimating the risks of a cyberattack isn’t worth sacrificing budget over, when now is the time to protect revenue and keep operations secure.
Additional reading
Bain and Company, Building Strategic Cybersecurity Capabilities After the Invasion of Ukraine, June 30, 2022
Cybercrime Magazine, 2022 Cybersecurity Almanac: 100 Facts, Figures, Predictions, And Statistics, January 19, 2022
Cybersecurity Insiders, 2022 VPN Risk Report, 2022.
Cloud Security Alliance, CISO Perspectives and Progress in Deploying Zero Trust. June 3, 2022
Economist Intelligence Unit & Pillsbury, AI & Cybersecurity: Balancing Innovation, Execution & Risk, September 9, 2021.
ESG and CrowdStrike, Walking The Line: GItOps and Shift Left Security, 2022
Forrester, The Forrester Wave: Endpoint Detection And Response Providers, Q2 2022, April 6, 2022 (Reprint courtesy of CrowdStrike)
Gartner, Forecast: Information Security and Risk Management, Worldwide, 2020-2026, 2Q22 Update, June 30, 2022. Client Access Required.
Gartner, Forecast: Information Security and Risk Management, Worldwide, 2020-2026, 3Q22 Update, September 15, 2022. Client Access Required.
Gartner, Forecast Analysis: Secure Access Service Edge, Worldwide, July 27, 2021. Client Access Required
KuppingerCole, Endpoint Protection Detection & Response, May 12, 2022
McKinsey and Company, Cybersecurity trends: Looking over the horizon, March 10, 2022
McKinsey and Company, Giving developers a leading role in cybersecurity Podcast, June 14, 2022
Okta, The State of Zero Trust Security 2022: Assessing identity and access management maturity in global organizations, September 2022
PwC, 2022 Global Digital Trust Insights Survey, opt-in, 31 pp., pdf, free.
PwC, 2023 Global Digital Trust Insights Survey, opt-in, 35 pp., opt-in.
World Economic Forum, Global Cybersecurity Outlook 2022. Published January 18, 2022.
World Economic Forum, The ‘Zero Trust’ Model in Cybersecurity: Towards understanding and deployment, Community Paper, August 2022
VentureBeat’s mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Discover our Briefings.





