A potential security flaw in iCloud Private Relay can lead Apple’s VPN to ignore firewall rules and send some data back to the iPhone maker’s servers.
This leak itself was first discovered by the VPN company Mullvad which was monitoring network connections while working on its own app.
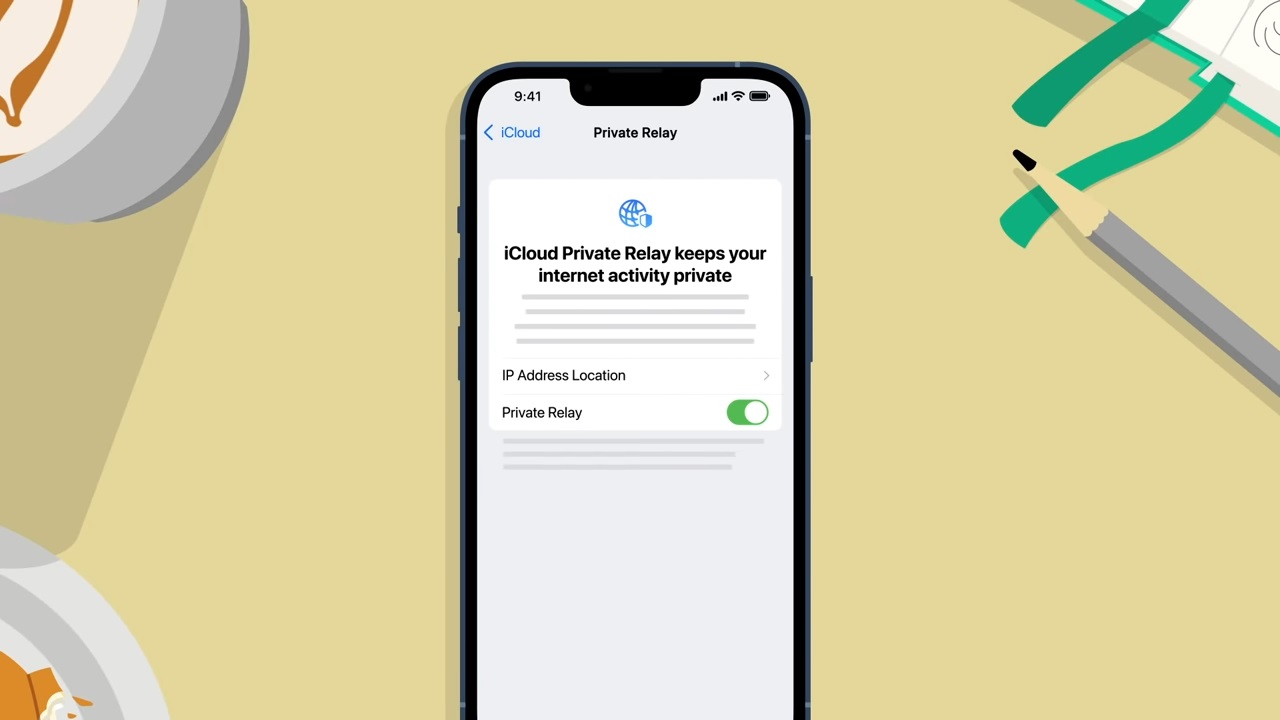
For those unfamiliar, Private Relay functions in a similar way to a VPN tunnel or how Tor works by routing a user’s encrypted network through relay servers before it reaches the internet. The service is currently still in beta and is only available in certain regions though it also requires a paid iCloud+ subscription.
TechRadar Pro reached out to Apple regarding this potential leak in iCloud Private Relay but we’ve yet to hear back at the time of writing. However, since the service is still in beta, this issue could be rectified before it becomes generally available. Since iCloud Private Relay’s beta release coincided with the launch of iOS 15, Apple could make the service available in full with the release of iOS 16 in September of this year.
Ignoring firewall rules
According to a new blog post from Mullvad, the VPN company was monitoring network connections when it noticed that QUIC traffic was leaving one of its computers outside of a VPN tunnel.
Disabling Apple’s Private Relay feature made the leaks stop and the company has even provided instructions so that other users can reproduce the leak on their own. Mullvad also pointed out in its blog post that Private Relay (mostly) disables itself as soon as any firewall rule is added to the Packet Filter (PF) system firewall on macOS devices.
As such, the company believes that the leak itself is just some kind of heartbeat signal calling home to Apple. Although it’s impossible to know what information is transmitted to Apple’s servers, the leak does send a clear message to both your local network and ISP that you might be a macOS user.
At this time, Mullvad is unaware of any way to prevent Private Relay from leaking user traffic back to Apple but the company recommends that users disable the feature altogether for the time being if their threat model forbids their local network or ISP from knowing what kinds of devices they’re currently using.
Via AppleInsider